Threat Intelligence Analysis of APT41
Executive Summary
An Advanced Persistent Threat (APT) can be defined as a sophisticated actor or group who conducts cyber-attacks in pursuit of various objectives which can include financial gain or espionage. The APT41 group (ID: G0096) is a Chinese state sponsored group that is associated with the name “WICKED PANDA” and conducts operations against a variety of sectors but mostly targeting the video game industry. The goals of APT41 have been observed to be theft of intellectual property and financial gain as the group has stolen source code, stolen digital certificates to sign malware, and deployed ransomware. The main tactics used by the group is delivery via phishing emails or exploitation of external facing assets to grain persistence and exfiltration of data. In September of 2020, two APT41 members were arrested and five other known members are currently fugitives in China.
APT41 Overview
Allegiances
According to the U.S Department of Health and Human Services (2019), APT41 is a “Chinese state-sponsored espionage group that has been active since 2012” (p.3). The group has been observed targeting several industries including technology, telecom, healthcare, and mainly the video game industry. The groups operations have been observed to coincide with several other sophisticated Chinese groups. As stated by MITRE ATT&CK “APT41 overlaps at least partially with public reporting on groups including BARIUM and Winnti Group” (MITRE). This indicates that APT41 does have access to other Chinese nation state actor resources and is closely linked to other groups. Two members of the groups have been arrested in August of 2020 while five other known actors of APT 41 are currently fugitives in China (Department of Justice, 2020).
Targeted Industries
APT41 has been observed targeting several industries, including conducting supply chain attacks to steal digital certificates to sign malware. Such as in 2017, the group attacked the popular utility CCleaner by Piriform where “[APT41] took the legitimate program and inserted malicious code that was designed to steal data from users” (Kaspersky). This CCleaner malware dubbed “Dirty Cleaner” was digitally signed by a Piriform certificate which made it more difficult to detect and harder for analysts to determine to be malicious. The other targeted industries by APT41 includes healthcare, technology, and commonly the video game industry. As stated by Mandiant, “The group’s financially motivated activity has primarily focused on the video game industry, where APT41 has manipulated virtual currencies and even attempted to deploy ransomware” (Mandiant, 2019).
Motivations and Goals
APT41 has the main motivations of theft of intellectual property via data exfiltration and financial gain through the use of extortion. As explained by Venafi, “The secondary goals of the attackers depend on the victim organization. In gaming-related organizations the group goes after personal or financial gain through manipulation or theft of in-game virtual currencies and attempts to deploy ransomware. With non-gaming victims, they go after intellectual property such as user, technology or clinical data” (Venafi, 2021). The group has also been observed stealing video game source code and in game items (such as virtual currency) to sell for profit.
APT41 Operational Analysis
Tactics, Techniques, and Procedures
APT41 has been observed a wide variety of tactics such as phishing or spear phishing to deliver payloads and exploiting vulnerabilities in public facing resources after conducting active scanning. The group has a unique technique of using self or stolen digital signatures for delivered malware to evade detection as previously mentioned above. After escalating privileges and laterally moving through networks, the group established command and control with domain generation algorithms until executing the action on objective by exfiltrating data or encrypting data. As stated by Venafi, “The secondary goals of the attackers depend on the victim organization. In gaming-related organizations the group goes after personal or financial gain through manipulation or theft of in-game virtual currencies and attempts to deploy ransomware. With non-gaming victims, they go after intellectual property such as user, technology or clinical data” (Venafi, 2021). APT41 has been observed combining these behaviors of attacking video game companies and stealing digital certificates as analyzed by Kaspersky Lab in 2013, “a Trojan was detected on a large number of computers – all of them linked by the fact that they were used by players of a popular online game. It emerged that the piece of malware landed on users’ computers as part of a regular update from the game’s official update server” (Kaspersky). The Trojan included drivers that were digitally signed from a signature that was stolen from another video game company.
Kill Chain
The kill chain of APT41 (see below) commonly starts with the group conducting recon through Open-Source Intelligence (OSINT) and gathering publicly facing system information through scanning. After delivery through phishing or a supply chain attack, the group gains persistence through various types of malware variants and collects data throughout the environment. After collecting the desired intellectual property, the group exfiltrates data through C2 channels, alternate protocols, or with low size limits to evade detection (MITRE).
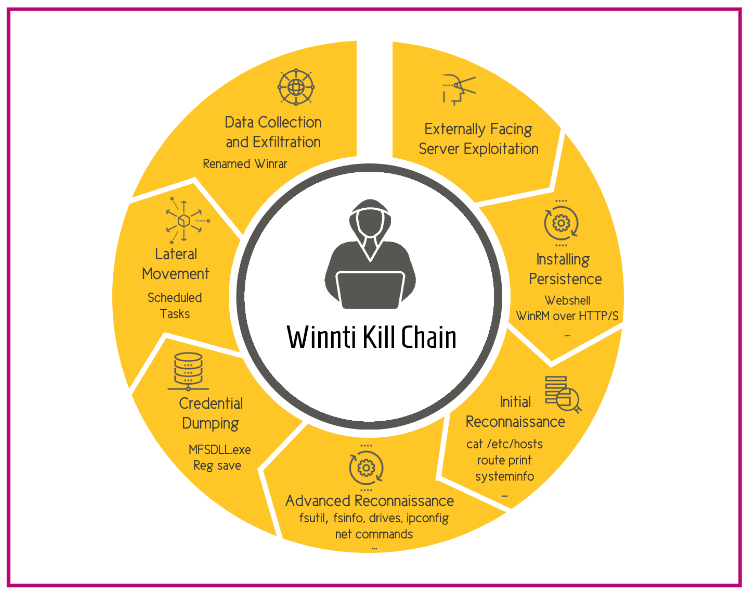
(Cybereason, 2022)
IOC Detection
A common piece of malicious software used by the APT41 is named “GEARSHIFT” and according to Malpedia is “a memory-only dropper for two keylogger DLLs. It is designed to replace a legitimate Fax Service DLL” (Malpedia). A keylogger is a form of malware that is a form of spyware, used to detect and transmit a user’s keystrokes to the attacker. This form of malware has had several iterations (see IOCs below) including a version that was digitally signed with signature that was stolen from a subsidiary of a target medical company.
GEARSHIFT IOCs:
File Name: 24BJCTGH.exe
Signature: win.gearshift
SHA 256: 4aa6970cac04ace4a930de67d4c18106cf4004ba66670cfcdaa77a4c4821a213
SHA 1: f3c222606f890573e6128fbeb389f37bd6f6bda3
MD5: f8c89ccd8937f2b760e6706738210744
References
apt41 perfects code signing abuse to escalate supply chain … - venafi. (n.d.). Retrieved October 10, 2022, from https://www.venafi.com/sites/default/files/2021-11/Venafi_WhitePaper_CodeSigningAPT41_2021_f_0.pdf
APT41. APT41, WICKED PANDA, Group G0096 | MITRE ATT&CK®. (n.d.). Retrieved October 9, 2022, from https://attack.mitre.org/groups/G0096/
ATT&CK® navigator - github pages. (n.d.). Retrieved October 10, 2022, from https://mitre-attack.github.io/attack-navigator/
Fraunhofer. (2019). Malpedia Win.Gearshift. Gearshift (malware family). Retrieved October 9, 2022, from https://malpedia.caad.fkie.fraunhofer.de/details/win.gearshift
Mandiant. (2022). Retrieved October 10, 2022, from https://www.mandiant.com/sites/default/files/2022-02/rt-apt41-dual-operation.pdf
Mandiant. (n.d.). APT41: A dual espionage and Cyber Crime Operation. Mandiant. Retrieved October 9, 2022, from https://www.mandiant.com/resources/blog/apt41-dual-espionage-and-cyber-crime-operation?utm_source=google&utm_medium=cpc&utm_campaign=PROD%7CAPT%7CNAM%7CEN%7CSearch&utm_content=all&utm_term=en&cid=global&gclid=Cj0KCQjw4omaBhDqARIsADXULuUvb_hwYWUQTQkxZxObyc_LJi2shQo3lwVFLrjHMMyG36_mkuMhZyMaAklIEALw_wcB
Nocturnus, C. (n.d.). Operation cuckoobees: Cybereason uncovers massive Chinese intellectual property theft operation. Cybersecurity Software. Retrieved October 9, 2022, from https://www.cybereason.com/blog/operation-cuckoobees-cybereason-uncovers-massive-chinese-intellectual-property-theft-operation
Seven international cyber defendants, including “apt41” actors, charged in connection with computer intrusion campaigns against more than 100 victims globally. The United States Department of Justice. (2020, September 16). Retrieved October 9, 2022, from https://www.justice.gov/opa/pr/seven-international-cyber-defendants-including-apt41-actors-charged-connection-computer
“Winnti” - media.kasperskycontenthub.com. (n.d.). Retrieved October 10, 2022, from https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2018/03/20134508/winnti-more-than-just-a-game-130410.pdf