Video Review
Key Points
Release Date: September 2021
Date Reviewed: February 2023
Author/Creator: Husky Hacks (https://huskyhacks.dev/)
Subject(s): Malware Analysis, Sandbox Lab Setup, Virtual Box, Reverse Engineering, Report Writing, Static Analysis, Dynamic Analysis, Windows API, Malware Techniques, YARA Rule Writing
Prerequisite(s): Familiarity With The Windows OS, Windows/Linux Command Line Experience, Basic Understanding of Programming
Medium: Video Course, Hands on Exercises, Written Content
Length: 9 Hours Video Content
Price: $30 Monthly Subscription (All Access Pass TCM Academy)
Link: https://academy.tcm-sec.com/p/practical-malware-analysis-triage?affcode=770707_o6lvcuwx (Affiliate Link)
Review Disclaimer
My goal is to provide honest and consistent reviews that can help others decide if an educational resource is right for them. Due to this, reviews are not influenced by discounts given, affiliate marketing, or if product is given for free. However, it is admitted that these benefits influence if a resource will be reviewed and that I only engage in partnerships with companies who provide quality products. If you decide a resource is right for you, it is very appreciated to use any noted affiliate links as this will help Cybersec.Reviews produce more content to further help students make informed decisions on their education.
Review
2023 pricing update
This course was originally reviewed when it was priced at $30 for the single course. TCM Academy changed to a $30 a month subscription based model later in 2023. This course has still been regularly updated and is considered a great value for the subscription.
Malware For Everyone
The Practical Malware Analysis and Triage course (PMAT) is available through TCM Academy and produced by Husky Hacks.This course dives right into the fascinating world of malware by having the student execute the infamous malware sample WannaCry which was estimated to have caused about $4 billion of economic losses (https://en.wikipedia.org/wiki/WannaCry_ransomware_attack). Prior to executing this malware sample, the student is guided through a detailed lab setup using Virtual Box, Flare VM, and REMnux. To be able to safely analyze a malware sample, the student is taught how to setup Flare VM on one machine and then REMnux with an internet simulator. These two virtual machines are connected and then isolated from the physical host which lets a student execute malware and analyze it’s resulting network traffic. Safety is stressed during this lab setup including techniques on how to handle malware samples that reduce the risk of accidental execution. After covering lab setup, taking snapshots, malware handling, and an overview of sourcing malware samples, the main course begins.
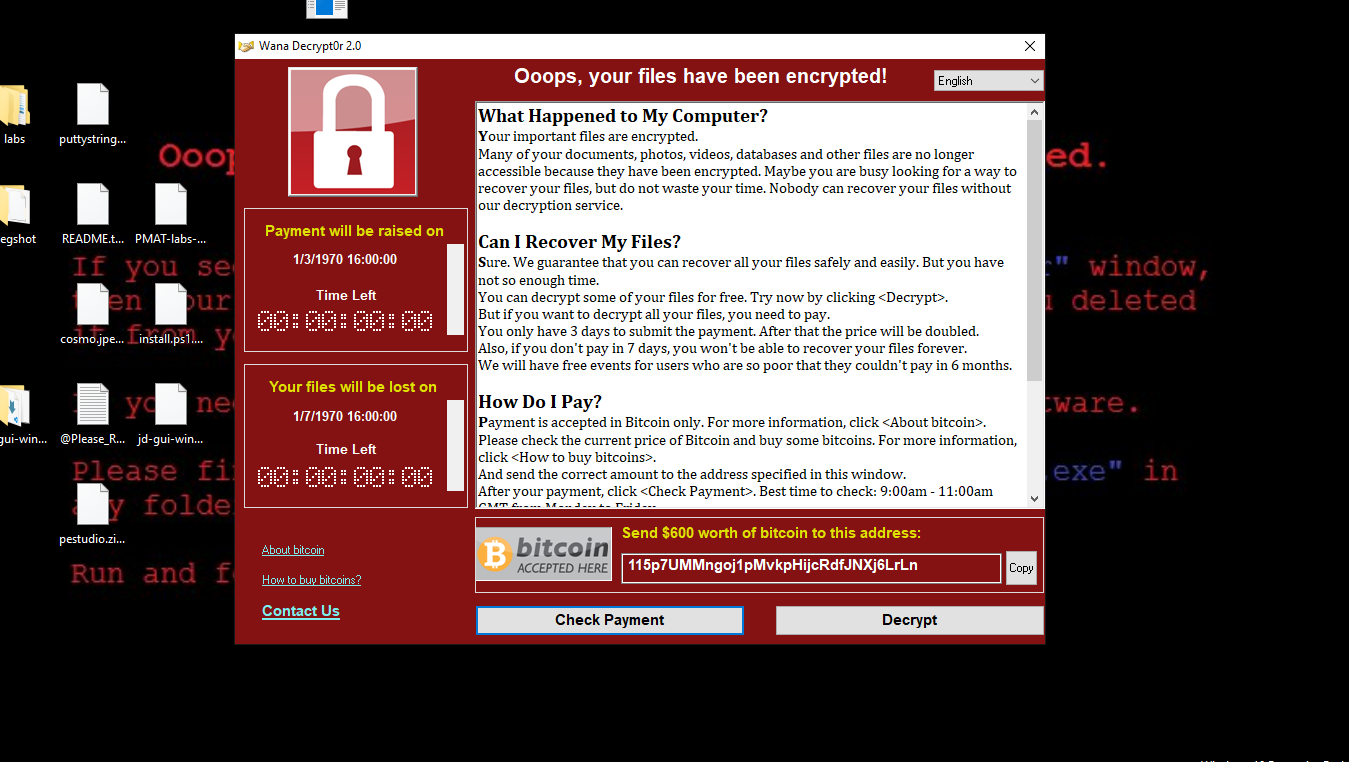
The main contents of the course is broken into 4 sections which include basic static analysis, basic dynamic analysis, advanced static analysis, and advanced dynamic analysis (see course curriculum with the link above). Each of these sections include a challenge that acts as an exercise for the student to practice the theory that was covered (more on this later). Basic static analysis involves gathering information from the malware sample without executing it, including interesting strings, the hash value, and more. Dynamic analysis is executing the malware sample and observing host and network indicators, such as processes being executed and HTTP requests. Advanced static analysis covers the basics of reverse engineering with the Cutter decompiler (again not executing it) and the advanced dynamic analysis is using a debugger to step through the binary. Some of the tools covered in this course include: strings, floss, PEStudio, Wireshark, Cutter, dnSpy, Process Hacker, MobSF, INetSim, x32/x64dbg, and YARA rule writing for detecting malware.
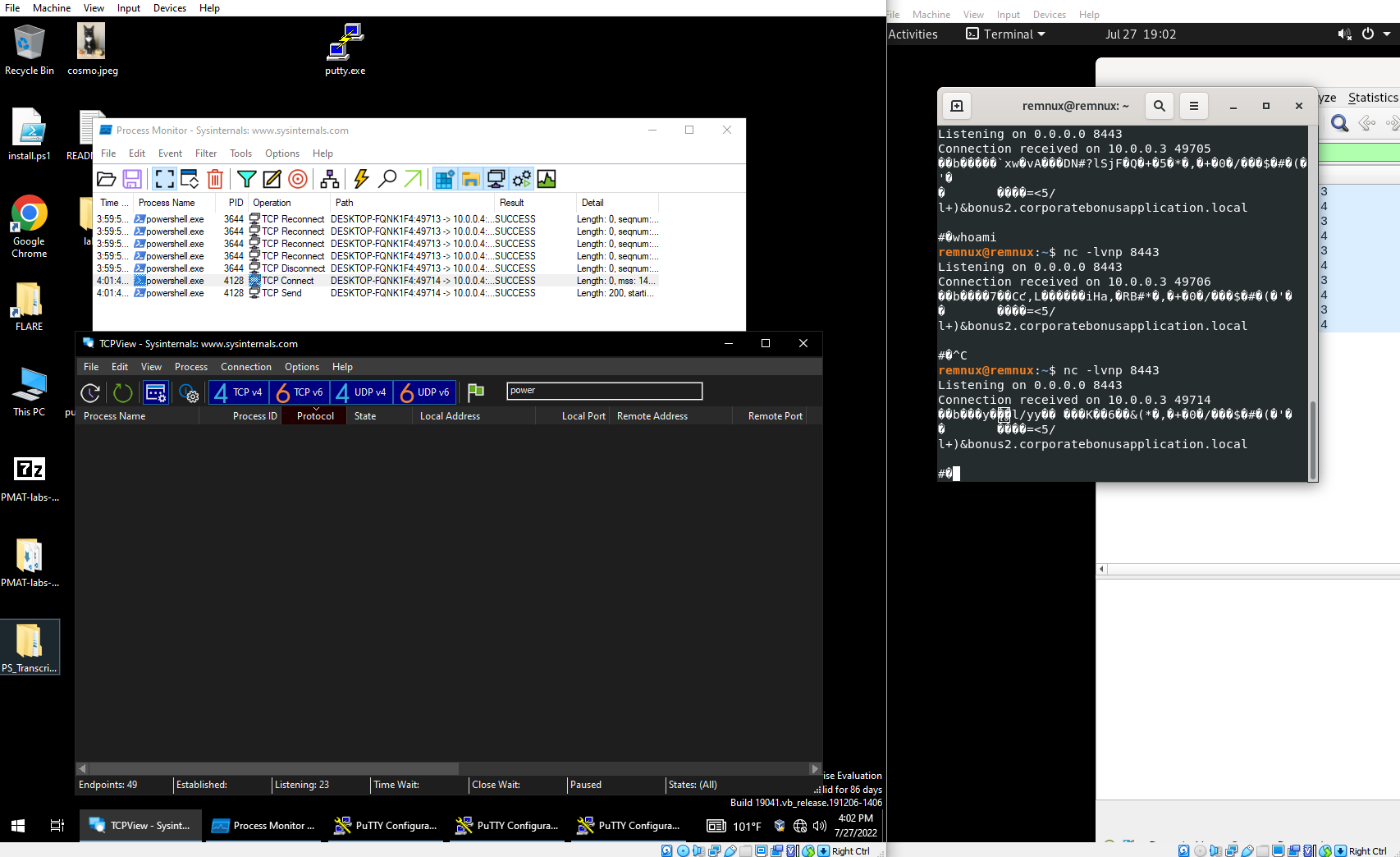
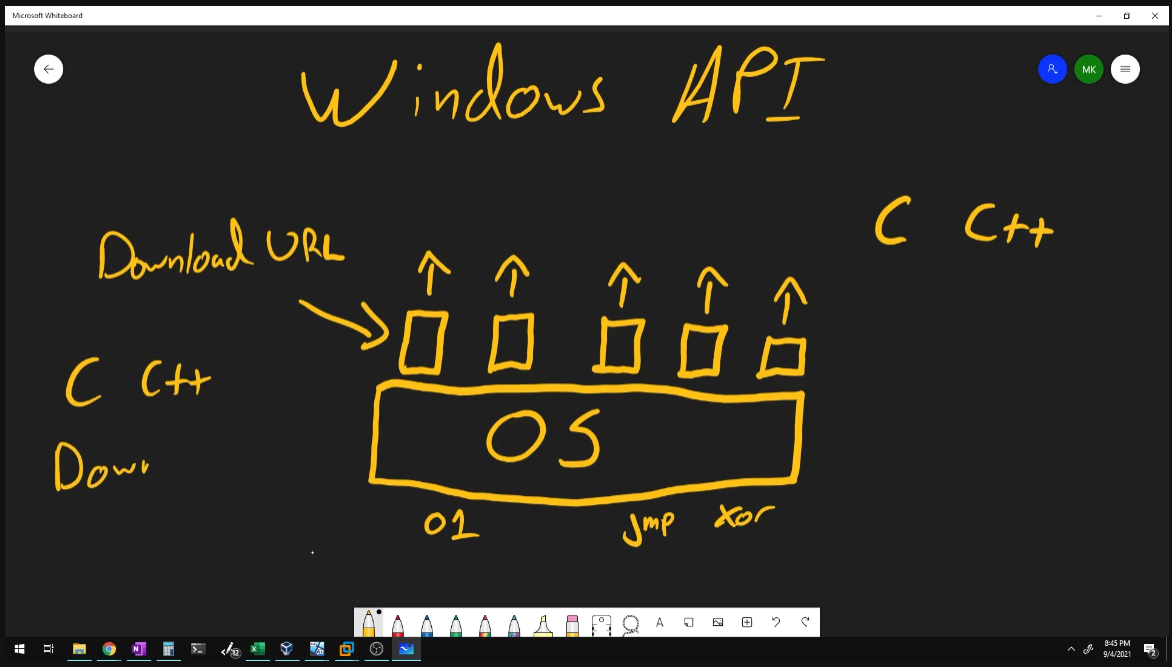
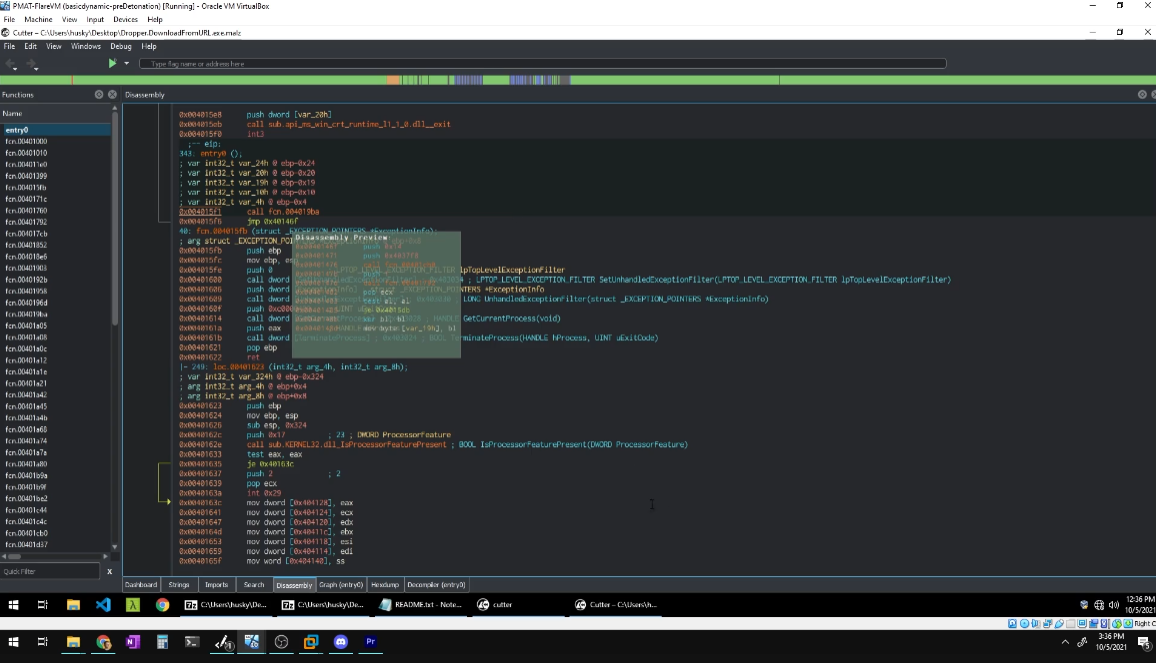
These subjects are taught with a mixture of theory with a “white board” approach and demonstrations the student can follow along with. Each subject is covered in a video that ranges from 8 - 20 minutes which I thought contained explanations that were delivered very clearly. Husky Hacks has a way of breaking down very complex topics that are easily digestible with the use of metaphors, visual illustrations, and easy to comprehend in-depth explanations. Although I did think the sections covering advanced analysis techniques were a little lacking and could have expounded the details of these subjects more. This led to conducting independent research of the x86 assembly language and concepts like the stack. However, later in the course I realized that this was unnecessary as the right amount of information is given to perform analysis on samples, but not too much that it would change this course into more of a reverse engineering course. The overall delivery of the information is well executed and is a great introduction to anyone interested in malware analysis and the basics of reverse engineering.
Getting Your Hands Dirty
Husky Hacks teaches with a process that begins with covering theory, proving examples, and then including an exercise the student partakes in as previously mentioned (for example https://github.com/HuskyHacks/PMAT-labs/tree/main/labs/1-3.Challenge-SillyPutty). These challenges are nicknamed “boss fights” and are a culmination of all the skills that were previously taught for the student to practice. I thought these boss fights were a fantastic way to get hands on keyboard practice since they also include challenge questions to help push the student in a direction while analyzing the malware sample. During these challenges, some questions include material that was not covered in the course and forces the student to partake in discovery based learning to attempt to figure out the answer. During these exercises, one could spend hours analyzing the malware sample that easily makes the actual length of this course double the 9 hours of video content the student watches.
After attempting to analyze a boss fight malware sample, Husky Hacks conducts a walkthrough. These walkthroughs were very useful and pointed out areas a student may be not comprehending and then to go back to study again. I previously stated that the advanced analysis sections felt lacking, but actually turned out to be the right amount of material delivered. I realized this while analyzing the advanced boss fight malware sample since the student was guided in answering questions that can be determined by understanding the basic logic of the malware sample. Prior, I was attempting to understand each and every assembly instruction, but in reality knowing only about 20% of what the logic is doing can give about an 80% understanding of the functionality (for these samples at least).
Specialty Malware Analysis Skills
After learning the fundamentals of malware analysis and putting it to practice, specialty topics and skills are covered. Some of these include, patching binaries to bypass anti-analysis, shellcode analysis, Powershell analysis, Microsoft documents analysis, mobile malware analysis, report writing, and much more. These topics are not covered as in depth as the previous sections but include many skills that gives the student a solid foundation to analyze other malware samples and also to conduct self research to discover new techniques. This section is wrapped up with an introduction to writing YARA rules to detect malware samples on a machine which helps the student build a complete methodology from analysis to detection.
Finally the course ends with the final boss fight and course final. The final boss fight is revisiting the WannaCry malware sample that was previously executed after the lab setup to again answer challenge questions. This final malware analysis challenge was a great way to end the course as it is a culmination of almost all of the skills the student was taught into one exciting exercise. Lastly, the course concludes with the course final project. This final is to write a comprehensive report on one of the included malware samples or another sample the student may be interested in. The main point stressed on this exercises is to use these analysis skills to deliver content that can be useful for the community, such as in a blog post. Again, this was a great way to end the course similarly to the WannaCry challenge as it lets the student revisit the skills previously learned to then write a report of findings and include IOCs with detection logic.
Conclusion
This course included everything I was looking for in a educational resource about malware analysis and much more. This course is also regularly updated at no extra charge (as recently as February 2023) which makes it even more value for the money spent. Husky Hacks is an excellent teacher who uses a mixture of theory, examples, and exercises that leaves the student feeling well informed. I am very excited to see what Husky Hacks produces next and will always check out his offerings in the future.
CSR Score
Quality: 5/5 Clear video and no audio issues. Any typos or mistakes are fixed or noted.
Education: 5/5 Great delivery of content with the inclusion of hands on practice.
Value for price: 5/5 At only $30 this excellent value for the money spent and includes more content being added.
Value for time: 5/5 The videos are concise and to the point which makes them not feel like they are dragging or a waste of time. The hands on keyboard practice is time well spent and is up to the students discretion.
Verdict
Total Score: 20/20 “A perfect resource of very high quality that is recommended to anyone who is looking to learn it’s subject”
(See scoring guide here http://cybersec.reviews/aboutme/#scoring)