Note-
This challenge write-up is a “blind analysis”, which was written prior to viewing the answer section of this course. I include how I answered questions, if I got it right or wrong, and why as a reflection for further learning. (Contains spoilers!)
Practical Malware analysis and Triage “WannaCry” Challenge
This write up comes from the PMAT course that was produced by Husky Hacks. My review of this course can be seen here- https://cybersec.reviews/reviews/tcmpmat/
The course is available here for $30 Monthly Subscription (All Access Pass TCM Academy)-
https://academy.tcm-sec.com/p/the-all-access-pass?affcode=770707_o6lvcuwx (Affiliate Link)
Challenge Intro
A challenger approaches! This is everything you’ve been training for, Analyst. Get in there and do your job!
In the early summer of 2017, WannaCry was unleashed on the world. Widely considered to be one of the most devastating malware infections to date, WannaCry left a trail of destruction in its wake. WannaCry is a classic ransomware sample; more specifically, it is a ransomware cryptoworm, which means that it can encrypt individual hosts and had the capability to propagate through a network on its own.
Perform a full analysis of WannaCry and answer the questions below.
Basic Static Analysis
OSINT
Starting with basic static analysis, I hashed the file and performed OSINT. Hash:e889544aff85ffaf8b0d0da705105dee7c97fe26
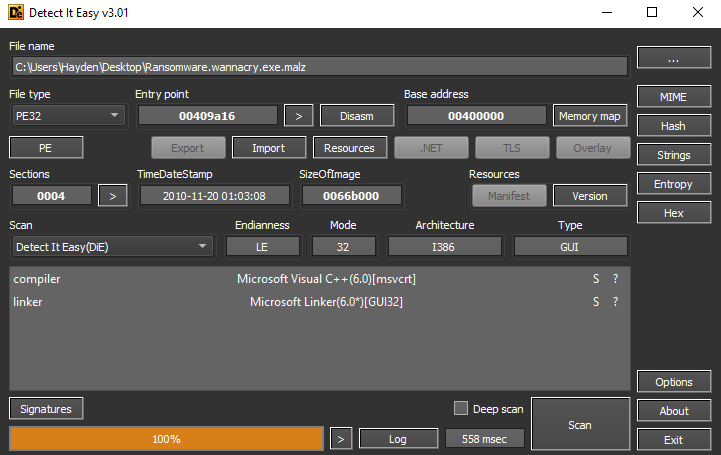
68/71 vendor detections, original name-lhdfrgui.exe, description-Microsoft® Disk Defragmenter, copyright- © Microsoft Corporation. All rights reserved. Contacts URL- http[:]//www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com/, eternal blue exploit.
tria.ge: https://tria.ge/230203-qw4c9afe63
10/10 score, 3MB size, wannacry malware famliy, worm, ransomnote with wallet “115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn”. TTPs- Deletes shadow copies, modifies user file extensions, drops startup file, contacts large amount of remote hosts, adds run key to start application, sets desktop wall paper
This information above indicates that I am looking for ransomware behavior, the use of an exploit named “eternal blue”, and a domain name of “iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea”.
Strings
Next, I searched for strings with the strings utility and FLOSS.
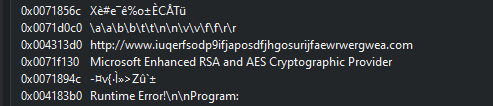
Some interesting strings I noted were- Lock Resource, ??1_Lockit@std@@QAE@XZ, Microsoft Visual C++ Runtime Library, IsDebuggerPresent, Microsoft Base Cryptographic Provider v1.0, C:%s\qeriuwjhrf, publicKeyToken=“6595b64144ccf1df”, http[:]//www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com File description says disk defragmenter.
The strings above has C++ being references, the previously observed domain, an interesting file description that appears to make the executable imitate a utility tool, the drive path “C:%s\qeriuwjhrf”, a public key token, and many indicators of encryption behavior (lock, cryptographic provider,lock resource). The IAT table also has similar function names and a “InternetOpenURLA” which is used to make an HTTP connection to a URL. This HTTP connection is noted and the previously found URL from OSINT and strings.
(URL From Strings)
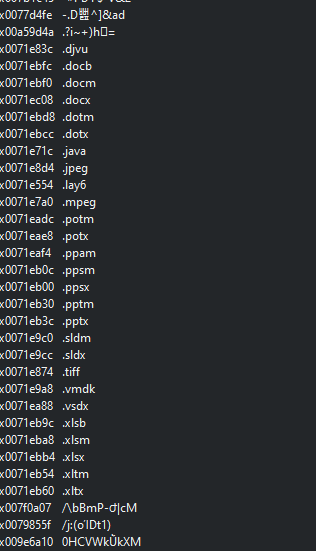
(File Extensions Strings)
Import Address Table
Next, I looked at the Import Address Table for interesting functions imported from DLLs.
Some interesting functions I noted were- CryptGenRandom, lockresource, Lockit@std@@QAE@XZ, ??2@YAPAXI@Z, InternetOpenURLA.
Dynamic Analysis
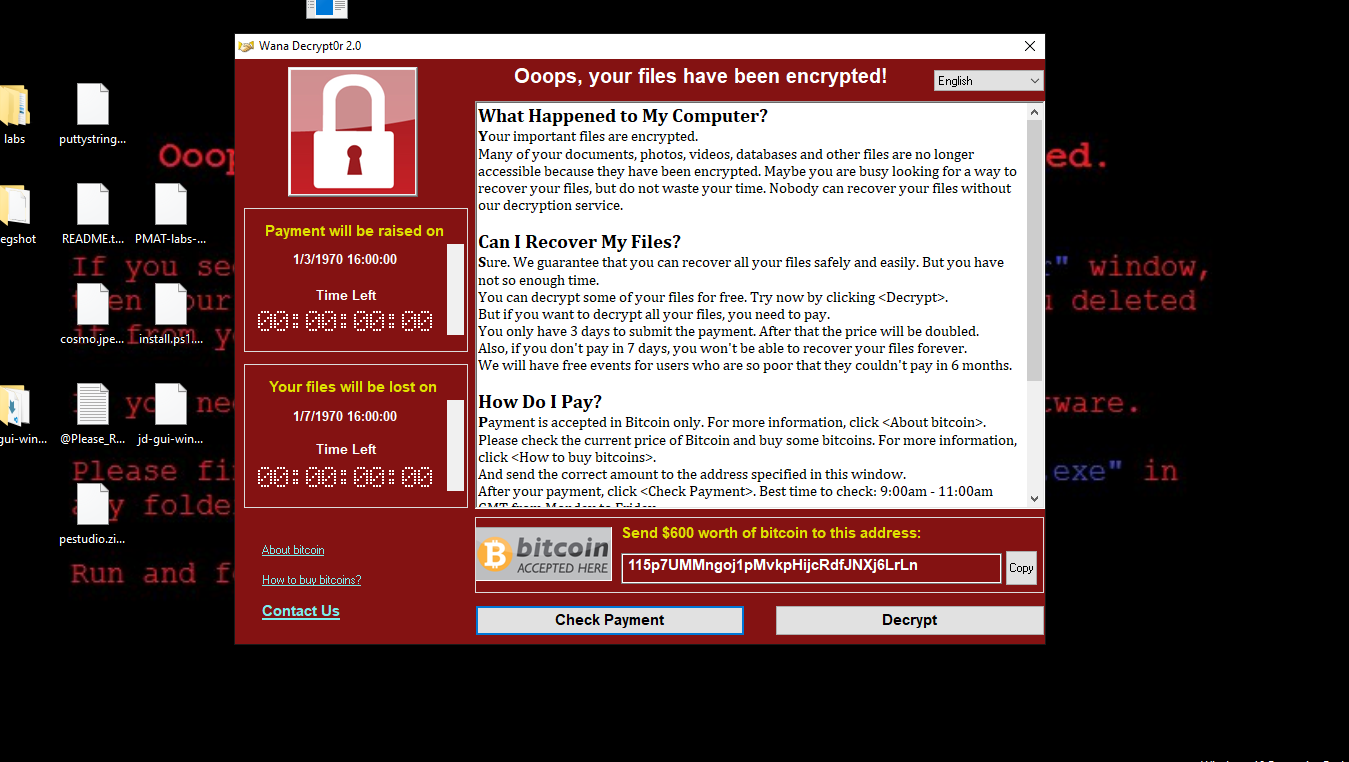
First I executed the sample without the INET simulator. The sample executed successfully and dropped the files “RANSOMWARE.WANNACRY.EXE-13727F84.pdf” and “\Desktop\Ransomware.wannacry.exe”. A DNS query was observed being attempted on the host with Wireshark to the domain “http[:]//www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com” about 5 times which received the response “destination unreachable”. The sample then proceeded to encrypt files with the extension “.wncry”, change the desktop background, drop a text file ransom note, and then display a window asking for bitcoin to unlock the machine. Using TCP viewer on the host machine, many connection attempts were seen to the IP addresses 169.254.x.7 over port 445. Port 445 is for Server Message Block services (SMB) for resource sharing.
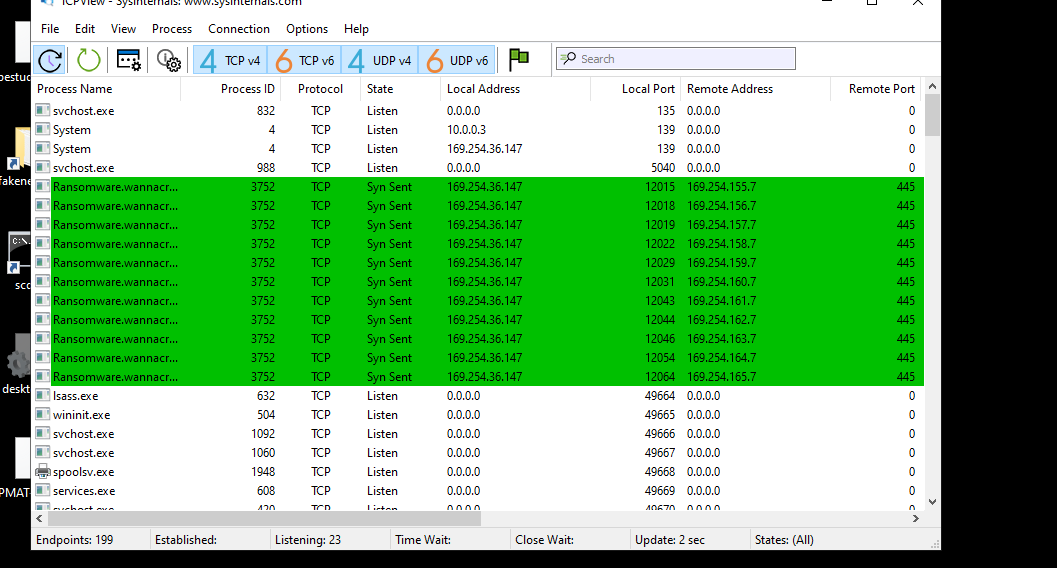
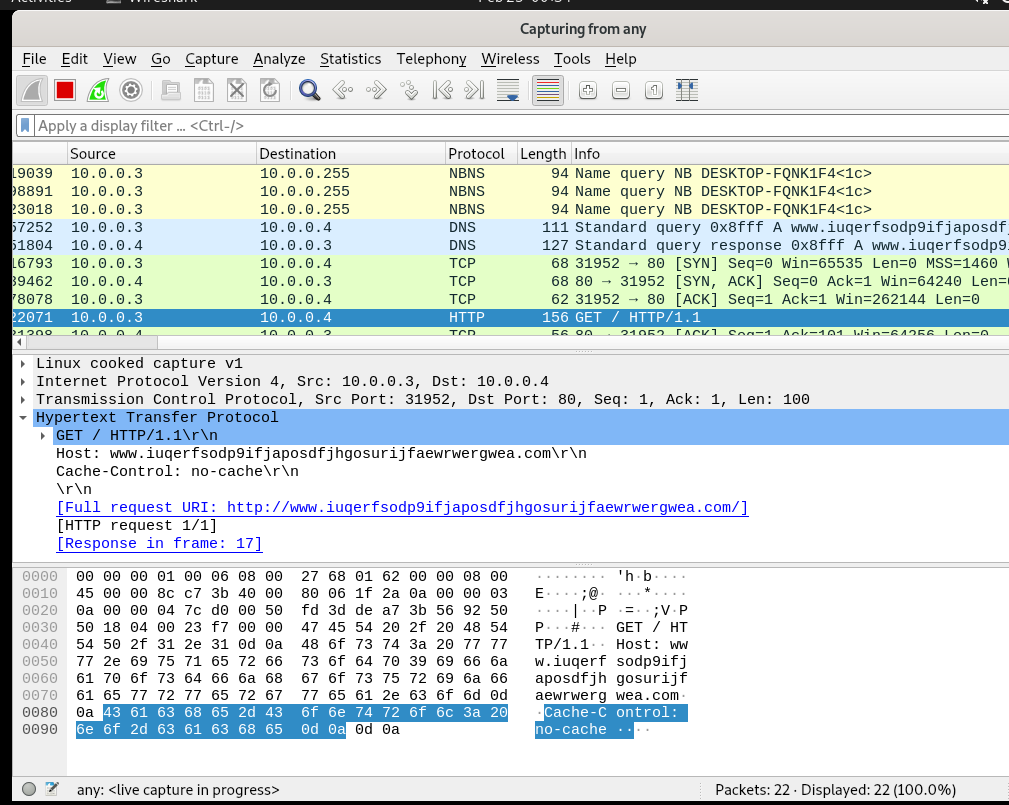
Next, I executed the sample with Inet sim running on my Linux machine. A HTTP request was again seen to to the URL “http[:]//www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com”. After a successful HTTP request, the malware exited and did not execute indicating this URL is a kill switch.
Advanced Static and Dynamic Analysis
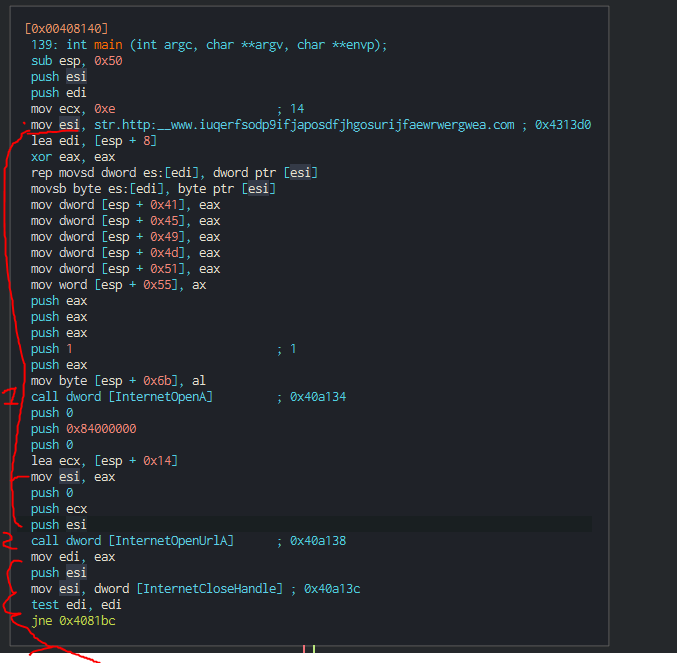
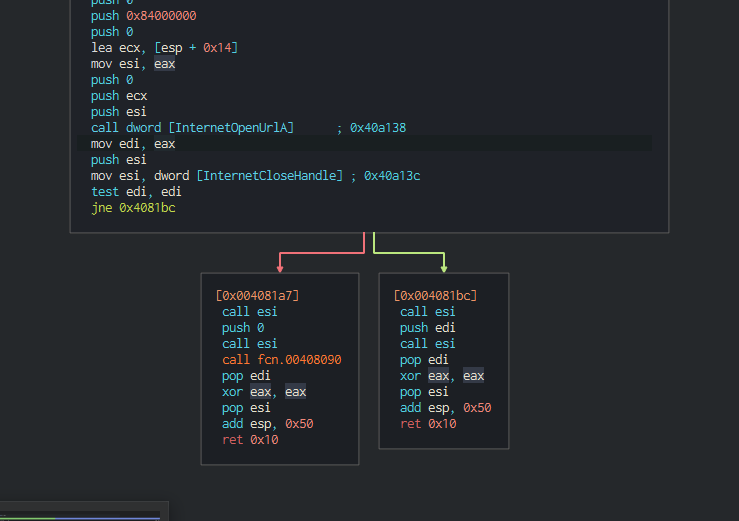
I opened the sample into the disassembler/decompiler Cutter. Looking into the main function I noticed that it pushes 5 parameters before calling “internetopenA” (1) which lets the application use the windows API for FTP or HTTP protocols. Next, it calls the internetOpenUrlA function to the URL which is now in esi (2- note this is incorrect and stated below in the challenges questions). This function specifies “Returns a valid handle to the URL if the connection is successfully established, or NULL if the connection fails”. esi is the last parameter to be pushed for the parameter “hInternet” and contains the URL string.
(Kill Switch Assembly)
Next, it calls the function “InternetCloseHandle” with only 1 parameter “hInternet” which is the handle to be closed “esi”. This function states “Returns TRUE if the handle is successfully closed, or FALSE otherwise.” It test edi against itself. This is not testing the register for the same value, but a bitwise operation to test wether the contents of edi are zero. If the contents of edi are zero than the zero flag is set. If edi is not zero, then zero flag is cleared.If the handle is true or 1, than the execution continues into [0x4081bc] with the jump if not equal instruction. If the handle is false meaning a connection failed, then execution will continue into [0x004081a7].
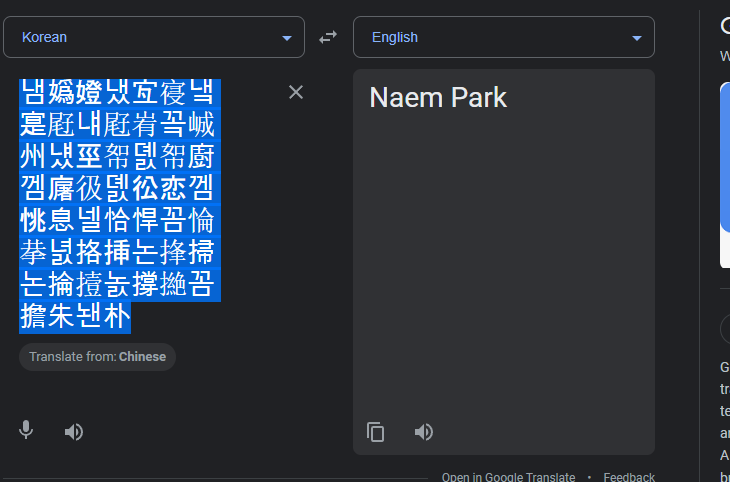
Another observation from the string output of Cutter showed a large number of characters in a different language (possibly Korean?). I first tried to translate the characters with Google Translate, which auto detected it to be Korean or Chinese. I then tried translating the text in different chunks or reversing it, but no attempts created comprehensive english. After playing around with it I finally got a translation to state “Naem Park”. Although it could just be a coincidence, the first thing I remembered that “Park Jin Hyok” who was a part of Lazarus Group was charged for cyber crimes including Wannacry (https://www.justice.gov/opa/pr/north-korean-regime-backed-programmer-charged-conspiracy-conduct-multiple-cyber-attacks-and). Again, this weird find is probably not related at all but its an interesting string of text either way.
A Note On IPC and Pipes
Lastly, I observed the string “\192[.]168[.]56[.]20\IPC$ and “SMB2” being noted. From previous knowledge of the Eternal Blue exploit, I recalled that this must be related to the use of this exploit for worm propagation. The “IPC$” is a Windows administrative share that is hidden as denoted with the “$” . It stands for “Inter Process Communication” and allows processes to communicate with other computers on the network. IPC uses Server Message Blocks (SMB) for network file sharing with other computers on the network that allows remote printing or drive shares. IPC also uses anonymous pipes for communication between processes on the same computer and named pipes for communication between different computers in a network (https://learn.microsoft.com/en-us/dotnet/standard/io/pipe-operations). For example, when a user unlocks a domain joined Windows workstation “winlogon.exe” sends the request over a named pipe to the Local Security Authority process (LSA) which then communicates to “lsass.exe” over a named pipe. Lsass then communicates to “netlogon.exe” over a named pipe for password verification since the host is domain joined. SMB and named pipes both use IPC but have different use cases. Named pipes are low level “message focused” and SMB is high level resource sharing.
Eternal Blue used a vulnerability in SMB version 1.0 that allowed an attacker system to perform a buffer overflow over SMB to conduct remote code execution on a target machine. This was seen previously during Dynamic Analysis.
Patching
I decided to verify the network connection theory by patching the binary. To do so, I changed the previously mentioned “jne 0x4081bc” (jump not equal) assembly by reversing the jump to a “je”. I then detonated the malware as an admin without INET simulator running. An HTTP request was seen to the URL which failed, but now the processes exited as seen before when it was successful. This verifies that the URL is acting as a kill switch when connection is successful.
IOCs
Hash: e889544aff85ffaf8b0d0da705105dee7c97fe26
URL: http[:]//www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
Dropped File: RANSOMWARE.WANNACRY.EXE-13727F84.pdf
Challenge Questions
Question: Record any observed symptoms of infection from initial detonation. What are the main symptoms of a WannaCry infection?
My Answer:
Main symptoms are the locked files, text file containing instructions, the window asking for bitcoin to unlock the machine. The background changes to also include instructions. The machine becomes very slow and many operations are conducted and the disk becomes very active. File extensions were changed to “.wncry” that were encrypted.
The Correct Answer::
Changed wallpaper on the infected host. A program window indicating the host has been infected that has a countdown timer and pay buttons. Encryption of files on the host’s file system. Files are encrypted and appended with a .WNCRY extension. The appearance of a @WanaDecryptor@ executable and a @Please_Read_Me@ text file on the desktop.
Self Grade: Correct findings.
Question: Use FLOSS and extract the strings from the main WannaCry binary. Are there any strings of interest?
My Answer:
Lock Resource, ??1_Lockit@std@@QAE@XZ, Microsoft Visual C++ Runtime Library, IsDebuggerPresent, Microsoft Base Cryptographic Provider v1.0, C:%s\qeriuwjhrf, publicKeyToken=“6595b64144ccf1df”, http[:]//www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com, C:\%s\qeriuwjhrf, Microsoft Visual C++ Runtime Library, \\192.168.56.20\IPC$, \\172.16.99.5\IPC$
The Correct Answer:
The most interesting strings are URLs. FLOSS identifies one that is built on the stack at runtime (a stackstring) that contains a long, unpronounceable website name.
http[:]//www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
Other strings of interest include UNC paths that call to different remote shares (\192.168.56.20\IPC$, \192.168.56.20\IPC$), a bunch of language pack files in a msg directory (msg/m_korean.wnry, etc), and the following:
%s -m security C:%s\qeriuwjhrf tasksche.exe icacls . /grant Everyone:F /T /C /Q WNcry@2ol7
Self Grade: Semi-correct. I missed the use of “tasksche.exe”, “icacls . /grant Everyone:F /T /C /Q”, and the language pack files.
Question: Inspect the import address table for the main WannaCry binary. Are there any notable API imports?
My Answer:
CryptGenRandom, lockresource, Lockit@std@@QAE@XZ, ??2@YAPAXI@Z, InternetOpenURL
The Correct Answer:
Interesting API calls include:
CryptGetRandom CryptAcquireContextA InternetOpenA InternetOpenUrl CreateServiceA ChangeServiceConfig2A
Self Grade: Semi-correct, I missed the use of a few functions.
Question: What conditions are necessary to get this sample to detonate?
My Answer:
The malware detonates after execution with no internet connection. Patching the jne in the binary-. jne > select > edit > reverse jump. Detonated the malware and no execution was seen. This verifies that if the URL is contacted than it acts as a kill switch.
The Correct Answer:
The binary attempts to initiate a connection with the weird URL http[:]//www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
If a connection is not established, the rest of the ransomware payload is executed.
If a connection is established, the program exits without executing the rest of the ransomware payload.
In a lab setting, this means that INetSim must be turned off in order to detonate the sample.
Self Grade: Correct.
Question: Network Indicators: Identify the network indicators of this malware
My Answer:
Upon detonation the sample contacts the URL “http[:]//www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com”. If an HTTP request is successful it exits. If the request is not successful, the sample tries to connect to internal IP addresses over port 445 for wormification.
The Correct Answer:
Attempted access of the weird URL. A flood of numerous SMB connection requests to private addresses. A secondary process, taskhsvc.exe, opens port 9050 to a LISTENING state and attempts to connect to non-private remote addresses over HTTPS.
Self Grade: Semi-correct. I missed the use of “taskhsvc.exe” and the open port.
Question: Host-based Indicators: Identify the host-based indicators of this malware.
My Answer: The file “RANSOMWARE.WANNACRY.EXE-13727F84.pdf” being written and a large amount of disk activity due to encryption.
The Correct Answer:
A new directory with a random character name is created in C:\ProgramData. The directory is set to hidden. This new directory contains many unpacked artifacts from WannaCry’s initial detonation. The artifacts include the taskhsvc.exe executable and a “Tor” directory that unpacks a “tor” program. A new service is created to start tasksche.exe as a persistent executable.
Self Grade: Incorrect. I completely missed this observation and will have to review the walkthrough given by Husky Hacks.
Question: Use Cutter to locate the killswitch mechanism in the decompiled code and explain how it functions.
My Answer: From my analysis above during the advanced static analysis, I noticed “internetopenA” was used and placed in the esi register. It then calls the function “InternetCloseHandle” which returns a true or false if the handle is closed or not for esi. It then tests the register edi against itself if the contents of edi are zero. If the handle is true or 1, then execution continues into [0x4081bc] with jne instruction. If the handle is false or 0, then execution continues.
The Correct Answer:
The killswitch operates like this:
In the main function of WannaCry, the string of the killswitch URL is moved into ECX. The arguments for InternetOpenA are pushed onto the stack. The boolean result of InternetOpenA is moved into EAX. The arguments for InternetOpenUrlA are pushed onto the stack, including the killswitch URL. The result of InternetOpenUrlA is moved into EAX. Then, this result is also moved into EDI. The handle is closed and the program compares the value of EDI to 0 (comparing a boolean true or false). If the value is 0, WannaCry makes a call to the first function in the payload. Else, WannaCry exits without triggering the payload.
Self Grade: Semi-correct. I understood the overall logic but missed which register had which value, possibly when one register loaded a value into another that I did not note.
My Takeaways
- The first thing I noticed I missed from the challenges questions was my observations on other processes such as “taskhsvc.exe” and the executable opening a listening port. In the future I’ll note to check for other processes and the host opening any out of ordinary ports on execution.
- I missed the hidden directory being written, I will have to watch for file creation events more carefully. Conducting analysis on this binary was difficult due to it encrypting the host machine on successful execution.
- Take more screenshots.