Summary
Credits
Hayden @CybersecReviews
Anna
Moose
Overview
Sample Hash: d7c808bceb5752abbe1e56151e8ac382a6dd94a4ff1499d14baef362e4cf08a0
Sample Name: RuneLite Stealer
Capabilitie(s): Information Stealer (RuneScape Credentials)
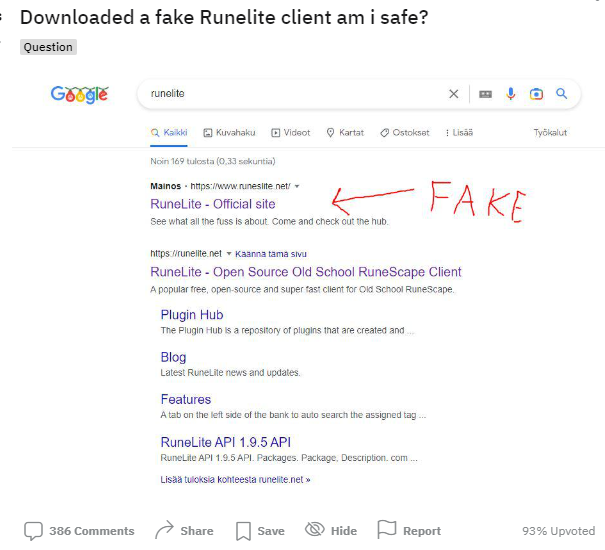
A friend of mine came across this Reddit thread that was posted on December 15th, 2022 and shared with me that he was attempting to view what the executable was and how it works. The malware sample was a modified game client for Runescape called RuneLite. Runescape is popular online MMO game that I played a lot in middle school and investigating a possible malware sample was intriguing to me. After performing analysis we determined that the main goal of this malware is to steal players credentials for Runescape. After a search for published work similar to our sample returning no results, we unimaginatively decided to name this malware sample “RuneLite Stealer”.
(https://www.reddit.com/r/2007scape/comments/zmvqq5/downloaded_a_fake_runelite_client_am_i_safe/)
Interestingly the executable was from a domain that was promoted with Google Ads for a “Rune Lite Client” that is used for RuneScape. As you can see from the Reddit post the fake domain and real domain are very similar and is typo squatting with an extra “s” (runeslite[.]net vs runelite[.]net). As you can see from the screenshot below, the fake website looks almost identical to the real version and utilizes links from the real website other than the download link which delivers the malware. All this, combined with the sponsored link would make it very easy for any user to mistakenly download the wrong executable.
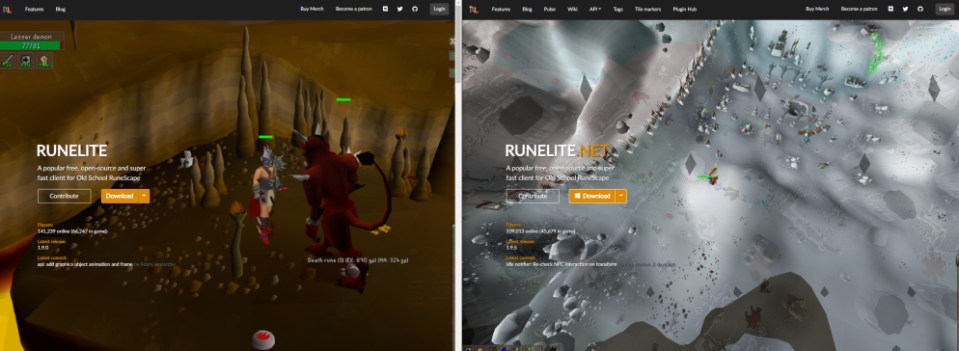 (Malware page on the left real website on the right)
(Malware page on the left real website on the right)
Technical Overview
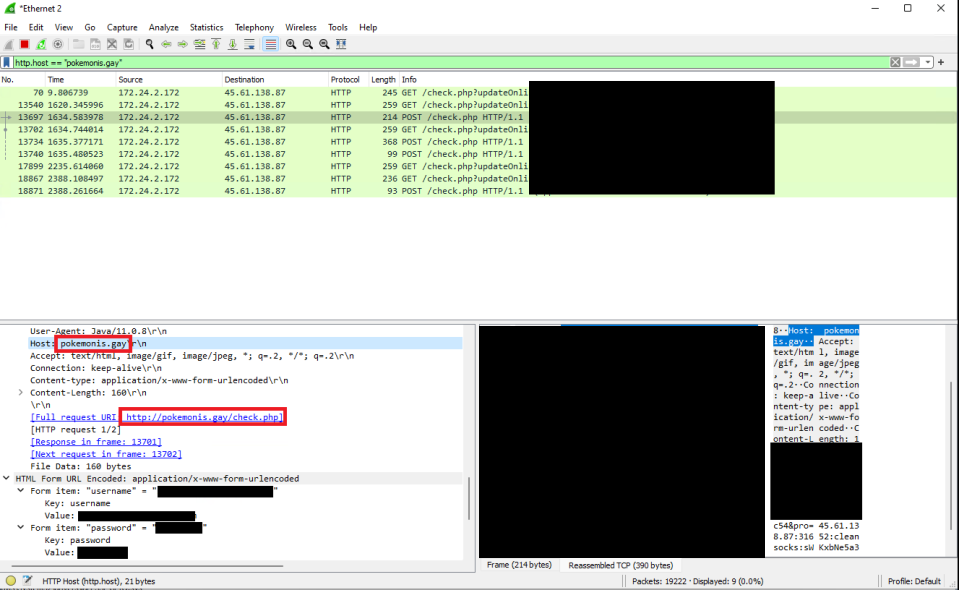
This malware sample is based off of a real RuneScape game client that is open source and free to use (https://github.com/runelite/runelite). The malware sample is very similar to the open source version including the installer, client GUI, and included files. The sample includes an installation file which when installed includes the malicious modified client. Upon executing the modified client, outbound requests are seen to the domain “pokemonis[.]gay”. When a user enter credentials, these are also forwarded to the same domain.
Analysis
Basic Static
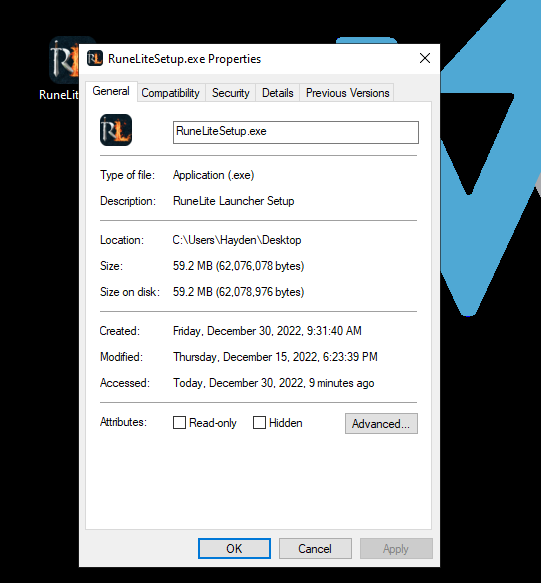
The malware is composed of the first file the user downloads named “RuneLiteSetup.exe”. After installation of this file, the user will have the “Runelite.exe” executable to run the modified client. The executable “Runelite.exe” includes a “config.json” file that points to the “RuneLite.jar” file in its directory. The “RuneLite.jar” includes the credential stealer ability in the included Java classes. Viewing the hash value for the setup file showed little threat scoring and included the “pokemonis[.]gay” domain under the Communicating files section. Pulling stings from the “RuneLiteSetup.exe” we noticed the strings “client.oprs” which is another RuneScape client called OpenOSRS (https://github.com/Rune-Status/open-osrs-client) suggesting this malware forked this repository.
(RuneLite malware installation)
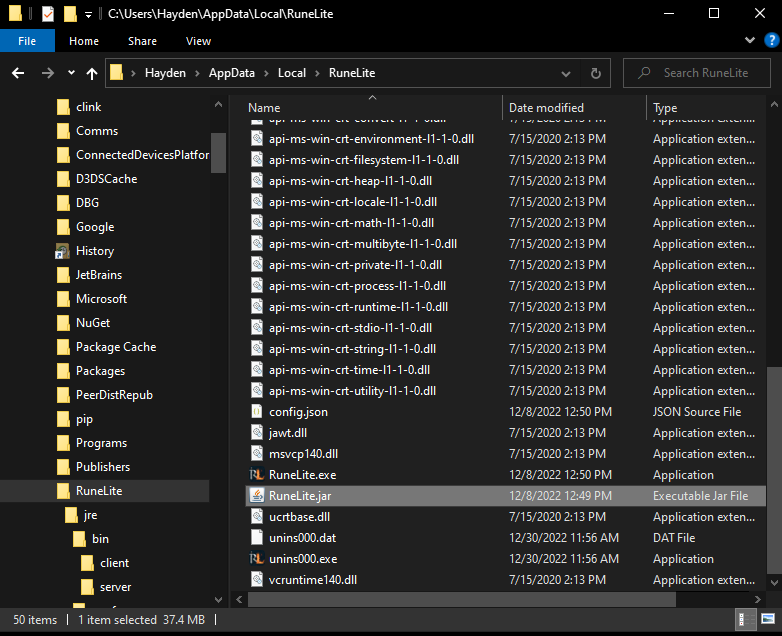
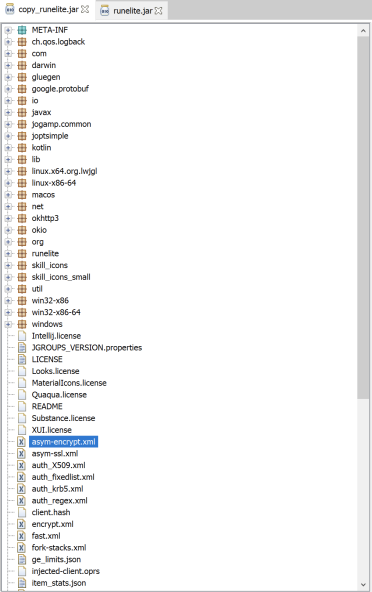
After installation, the files are located in the path “C:\Users\Username\AppData\RuneLite”. The folder contains many files including DLLs, a un-installation file, the client executable, and .jar files. Not having much experience with Java or how .jar files worked these were a little confusing on how these files were utilized by the client executable. Opening the .jar files in a Java disassembler tool such as “JD-GUI” (http://java-decompiler.github.io/) revealed the contents of the config and Runelite jar files. The Java file has many classes including the class “okhttp3” which included the credential harvester ability seen below.
String usernameAndPassword = username + ':' + password;
String encoded = ByteString.Companion.encodeString(usernameAndPassword, charset).base64();
return "Basic " + encoded;
Viewing more classes in the .jar file also shows a class called “unethicalite” which is another open source RuneScape client (https://github.com/unethicalite) that is commonly used for making RuneScape bots and cheating and is stated to charge users $15 a month to use seen in the link below. (https://www.reddit.com/r/RunescapeBotting/comments/xodeeh/are_there_any_3rd_party_clients_such_as_openrs/).
Dynamic Analysis
Executing the file “Runelite.exe” shows a login screen identical to the RuneScape Lite client, which again would appear normal to any user. Upon entering credentials, an outbound POST request is observed to the same domain “pokemonis[.]gay”.
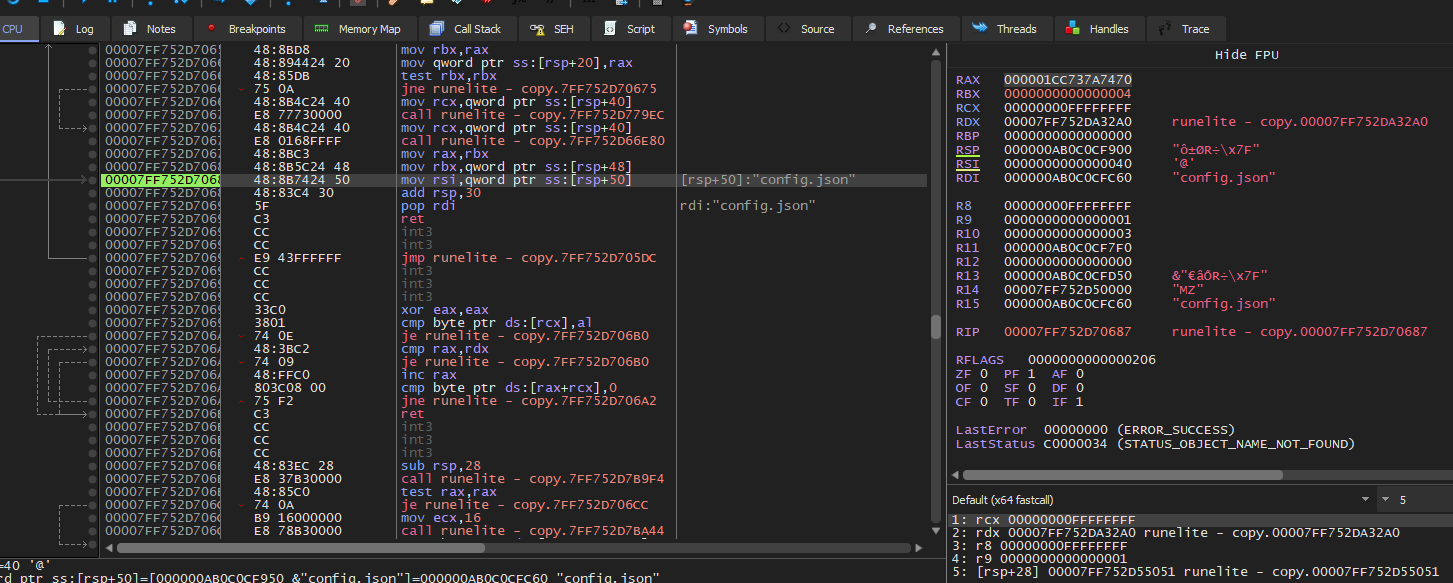
Advanced Static & Dynamic Analysis
Again not being familiar with how .jar files interact with compiled executables, viewing the file “Runelite.exe” in a debugger or a decompiler does show the “config.jar” file being refrenced.
Detection
IOCs
RuneLiteSetup.exe:d7c808bceb5752abbe1e56151e8ac382a6dd94a4ff1499d14baef362e4cf08a0
Runelite.jar:8c86e249cf49d39278e4cf9b51c9b75ef7c77f16a8211ce97261261beae2adb8
Domain: pokemonis[.]gay
Domain: runeslite[.]net
Takeaways
For Professionals
Due to the sample RuneLiteStealer only being a credential stealer for RuneScape players, this does not pose risk to an enterprise environment. However, letting users download video game related software on company systems does pose a risk as another malware variant could easily include much greater capabilities than seen in this sample. Also due to the method of delivery being via Google Ads, IT professionals should be aware and train users to not solely trust a website just because of it being promoted on search engines.
For Users
This analysis is not solely a lesson on the risk of downloading video game software but is a lesson on the risk of Google Ads being used for a method of delivery which is becoming more and more common (see https://www.bleepingcomputer.com/news/security/hackers-abuse-google-ads-to-spread-malware-in-legit-software/). For users it is recommended to validate the source of files before downloading. An example of this could be to look into the developers social media accounts which usually includes links directly to the correct website. Examples of this being (https://twitter.com/runeliteclient) or (https://twitter.com/OBSProject) and not solely trusting a search engines results.
If you believe you have downloaded “RuneLiteStealer” it is recommended to change your RuneScape account passwords and any other accounts credentials whereas you have reused the same password. Uninstalling the modified RuneLite client and running an antivirus scan is recommended.