Note: To protect the identify of individuals in this CTF. The missing person in cases are referred to as subject or subjects.
Overview
OSINT stands for Open Source Intelligence and is defined as, “the collection and analysis of data gathered from open sources (overt and publicly available sources) to produce actionable intelligence (https://en.wikipedia.org/wiki/Open-source_intelligence). Trace Labs (https://tracelabs.org) Offers a unique OSINT CTF that was very surprising to me when I came across it. Back in November of 2021 I was browsing my usual Discord servers and came across a post about a "Search Party CTF". Search Labs organize CTFs that crowdsource the OSINT skills of the hacker and tech community to help solve real missing person cases, Isn't that awesome? Instead of finding the usual flags for a CTF, points are awarded depending on the type of information one finds. For example, finding "Basic Subject Info" like social media accounts, blog posts, and more is awarded 50 points. While finding information relating to "Day last seen", like direction of travel, pictures, and other details is awarded 500 points each. If you would like to read more into the rules, check it out here https://download.tracelabs.org/Trace-Labs-OSINT-Search-Party-CTF-Contestant-Guide_v1.1.pdf . All of this information is gathered and then submitted to law enforcement to aid in investigations.
Preparations
I was stoked to find this CTF, one of my top enjoyments in life is to help others (hence cybersecurity) and I thought this would be a great opportunity. Three other students in the University of Arizona's cyber security club (Cyber Saguaros) and I formed a team. We tried to prepare by going over what OSINT resources we could find and I will have a section below of our most favorites. In my preparation, I originally thought this CTF would be a great opportunity to familiarize myself with the Dark web since there is a category for finding a subject's information on a .onion URL. This is not needed as the wealth of information you can find on the clear web on a subject is astounding and to be forward, you do not have to be technically inclined to participate in this CTF. You only need a web browser, Google, and a VPN if you want to add a layer of security.
The CTF
Prior to the start of the CTF a webcast was held to go over the rules of engagement and submitting reports. One big rule of this event is that you must do passive recon only. One example that was stressed is submitting password resets on a subject's profile, which might push an alert to the subject and/or his/her family. Next, reporting was explained. During the CTF a submission portal is opened which includes selecting the category of information, why it is relevant, a link to it, and optional screenshots. The report does not have to contain a wealth of information, concise and straight to the point is all that is needed. Each team is paired with a judge that reviews each piece of intel that is submitted and determines if it matches the criteria for submission. For example, when the CTF started I found news articles that contained information about family names of the subject. These submissions were all denied since "information from news articles or missing persons aggregate websites are not accepted since they are known to law enforcement". To be deemed as usable, this information would have to come from elsewhere, such as the subjects personal social media account follow list.
Methodology and intel
To be front, the main technique we used was Google and then pivoting off found pieces of information. Like finding a subjects social media username and then searching for this username in other areas since subjects commonly reuse them and then finding an address. We found more "common" pieces of information easily, including social media accounts, license plate numbers, employment, relationships, and acquaintances. Recalling the details are a little fuzzy since this CTF was about 2 months ago, but here is the more notable information that we found:
- One of the subjects is a highly active swimmer that was last seen in an area he/she/they frequented. Reading through reports and articles, it was never noted the weather conditions of the area around the time the person went missing. One of our team members came across a tweet by the cities weather account which included video of the bay area during a storm that had massive waves and an intense storm. The video was taken around the same area the subject was last seen and around the same day. This information was submitted and deemed useful by our judge for the "Day last seen" category.
- The next piece of intel was a submission of a YouTube account. The subjects account had a YouTube video uploaded of them weeks after he/she/they went missing. This was also deemed useful under the "Day last Seen" category.
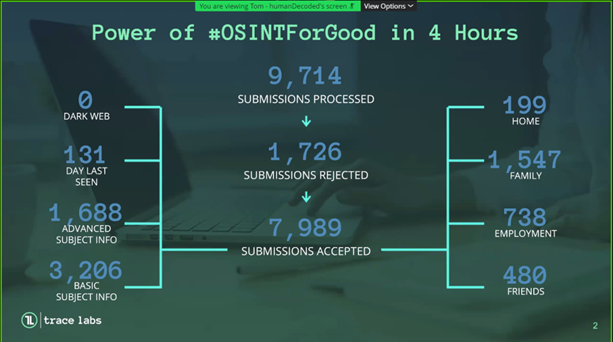
Trace Labs does offer an award for the "Most valuable OSINT" which regarded as the most significant piece of intel found during the event. The award went to a team that found a subjects vehicle posted for sale on Facebook marketplace shortly after running away. Also, another piece of intel that was noted was a team found a subject actively using an account after the date of going missing. Here is the total amount of information that was found by all teams in 4 hours:
The Dos
Here are my biggest takeaways from participating in this CTF for the first time.
- Read the trace labs contestant guide thoroughly.
- Create a temporary channel to communicate on, such as Discord.
- Get adequate sleep the night before and have food/water at the ready. Previous CTFs were 6 hours long and this one was shortened to 4. It felt very mentally draining and by the end of the CTF I was mentally burnt out.
- Determine who has special skills on your team. For example, it is common to have one person do most of the report writing and be the Point of Contact on a team due to a person's communication skills.
- Stay calm and stay focused. The minutes leading up to CTF I started to get nervous, I'm not sure if was a bit of imposter syndrome but I started to not feel prepared. Don't worry, you have multiple subjects to work with and if you feel like you're struggling then try to work with a different one. Also, don't worry about the scoreboard, you will find information and remember that it is for a good cause.
- Work with the information that is in front of you. Sometimes I would create a rabbit hole for myself and start speculating about types of information I could find and then focus on this. Instead, try to devote blocks of time to finding certain information. Such as devoting 10-15 minutes on trying to find subjects vehicle information, this removes the wasted time from creating a rabbit hole.
- One of our team members (and club leader whoo whoo!) Vetulia had this advice, "Learn your Google Fu, don't get attached to the cases. Mental health is super important so if the cases get too challenging, step back. Create a list of personal details to look up for each case."
The Don'ts
- Don't create your own red herrings. Again, use blocks of time to search for certain ideas. But make sure to not spend a lot of time searching for information that might not be there.
- Don't get emotionally attached. There were times I spent discussing and speculating about a subject's life and situation, bringing up feelings of sadness. Albeit this usually happened when I started to feel mentally drained or stuck. Focus on the data and if you need a break, then step away for a little. I never stood up from my computer for the 4 hours and this is something I later regretted. It feels counterintuitive but stepping away for a few minutes and then coming back is better than staying at your computer and feeling drained.
- Don't pester your judge. Sometimes it can take a while for a submission to be cleared for points or rejected. Judges have mountains of information to sift through, so be patient.
Takeaways
One of my takeaways from this event is the surprise of how much information is out there in the Clearnet. OSINT is very powerful and has its own wealth of tools, techniques, and methods to be mastered. I truly only used Google and one website to cross reference usernames, so I am going to try to study up on OSINT and try some tools. My next takeaway is on self-care. This can sound redundant but participating in this CTF was mentally and emotionally draining and it's easy to picture yourself or a loved one in the same situation as the subjects. Take breaks, get sleep, and make time for yourself to enjoy other hobbies besides computers. My last takeaway I had is about what security professionals can do for the world. We can not only protect users and systems, but we have the skills to do much good for the world. If you've never participated in a CTF I highly recommend checking out Trace Labs and studying any OSINT resources that appear to be helpful for you. Who knows, you might become addicted and become a missing person OSINT master or look deeper into other more technical CTFs. I the end, Trace Labs is a great organization and I really appreciate the time and energy they put into their work.
Resources
- https://pentest-tools.com/information-gathering/google-hacking
- https://www.tracelabs.org/initiatives/osint-vm
- https://www.osintcombine.com/osint-bookmarks (This has pretty much everything you need)
- Linked in OSINT Techniques- https://www.youtube.com/watch?v=bz4oZBR3LEk&list=PLe4K-rcvfvGa9yOBTgQvhTeaDM4gsagj3&index=5&t=501s
- OSINT Overview and Techniques- https://www.youtube.com/watch?v=g5UHijJ_Jo0&list=PLe4K-rcvfvGa9yOBTgQvhTeaDM4gsagj3&index=10&t=610s
- Searching Data breaches- https://www.youtube.com/watch?v=UeI7wEdLPn8&list=PLe4K-rcvfvGa9yOBTgQvhTeaDM4gsagj3&index=23
- Track down Tinder profile with OSINT- https://www.youtube.com/watch?v=b7bpXlRHgqY&list=PLe4K-rcvfvGa9yOBTgQvhTeaDM4gsagj3&index=32&t=497s
- https://osintframework.com/
- https://github.com/jivoi/awesome-osint
- [https://kartaview.org]